Core Concepts and Processes
When we embarked on this research project, we began with the primary questions of what constitutes a digital identity system. In the last few years, with the rise in national digital identity projects, there has been significant academic and media attention to the idea, benefits and risks of a digital identity system. However, there have been relatively few attempts to critically look at what makes an identity system digital, and what are its defining elements and characteristics. Through a preliminary study of existing identity systems, we have arrived at these core set of concepts and processes that mark a digital identity system. In arriving at this list, we have relied upon and referred to the works by Dave Birch et al, World Bank’s ID4D initiative, Mawaki Chango, Kaliya Young and Kayode Ezike.
By publishing this, we hope to arrive at a shared vocabulary to discuss and critically analyse digital identity systems, both within our team and in engagements with other stakeholders. This illustrated and interactive glossary can serve as an easy reference for anyone seeking an introduction to the core aspects of digital identity. Even though this is essentially a list of definitions with examples, it does not follow an alphabetical order like most glossaries, but the logical flow of concepts as they build upon each other in a working identity system. We have paid special emphasis to the core processes of Identification and Authentication, elucidating them through diagrams.
Use the green links under the concept definitions to see how the concept is used in the core processes of Identification and Authentication. Within the process diagrams, use the text in green or the illustrated elements to navigate the document.
Use the green links under the concept definitions to see how the concept is used in the core processes of Identification and Authentication. Within the process diagrams, use the text in green to navigate the document.
Individual
Identity Systems are created in order to provide means of identification to an identified set of population, such as residents, citizens, individuals above a certain age etc. In the context of an Identity System, an individual is someone eligible to enroll within it.
Identity
Identity refers to a set of attributes of an Individual that can be used to identify them individually or as part of a group of individuals.
Identity System
An identity system comprises all the databases, processes, technologies, infrastructure, credentials, and legal frameworks associated with the collection, use, and management of personal identity data for the purpose of identifying individuals.
Identification ↓ Authentication ↓
Foundational Identity System
A foundational identity system is a core Identity System created to manage identity information for the general public, and to provide identity proof for a wide variety of public and private services. National ID systems such as Aadhaar in India or the e-ID scheme in Estonia, and population registries, are common examples of foundational identity systems.
Functional Identity System
A functional identity system is designed to meet the needs of an individual sector, and is not designed for other purposes or in other sectors, although in some cases, may be used for other purposes or in other sectors. For instance, a voter ID can designed specifically for use by the Individual for the purpose of proving their Identity while voting, just as a Tax ID number (or registration number) is designed for use while dealing with tax related matters. The National Health Service in the UK has its own digital Identity System to identify patients and keep records of their treatment.
Unique Identity System
A unique identity system is one that uniquely identifies individuals within a population, such that no one person may enrol multiple times in the system, and that each Identity Artifact is associated with only one person. For instance, the Aadhaar scheme in India has ensured that each Unique Identification Number in the system is only associated with one individual, through the process of de-duplication.
Centralised Identity System
A centralised identity system is one in which there is a single recognised agency or body, which is tasked as the issuer of identity. The e-ID system in Estonia or the NADRA in Pakistan, for instance, entails one government agency responsible for providing identification and authentication services for individuals, without the Individual being able to choose which entity to enroll with.
Federated Identity System
Under a Federated Identity System, multiple digital ID providers, who may be public or private, are endorsed by the Identity System. Here, individuals can choose between these digital providers, and use the issued credentials for a wide range of services through an identity hub or a gateway that facilitates authentication across multiple platforms.
In a Brokered Identity Provider model, identification and authentication are carried out by multiple digital ID providers, but with the additional presence of a central hub through which data is exchanged. An example of this is the Gov.UK Verify ID system in the UK, which allows individuals to choose between several different certified private identity providers to access a range of public and private services.
Open Market Identity System
In an open market system, public and private organizations create, use, and manage their own digital identities according to a self-regulated framework. Here, there is no central scheme, and the digital identities can be used to access government services only where there are agreements between the government agency and the identity services provider.
Self Sovereign Identity System
In a self sovereign identity system, each Individual or entity can be empowered to create unique, digital and portable identities on their own which can rely on decentralised technologies such as shared ledgers for use, but do not rely on any centralised authority, rendering them irrevocable by any third party.
Interoperability
Interoperability is the ability of different functional units—e.g., systems, databases, devices, or applications—to communicate, execute programs, or transfer data in a manner that requires the user to have little or no knowledge of those functional units. An interoperable system is one whose interfaces are understood, to work with other products or systems, present or future, without restrictions.
Identification
Identification is the process of establishing the digital identity of an Individual and ascertaining information about them, by verifying corroborating documents, testaments, and other forms of proof of the Individual’s claimed Identities and Attributes. In the context of a digital ID System, this may involve individuals first claiming certain Attributes (such as their name, sex, date of birth etc) and having them recorded, then presenting requisite documents or testaments to validate their Identity Claim. Finally, they are issued certain credentials (such as PINs, ID Cards etc) or their Attributes are accorded the status of ID credentials (such as biometrics) which can be digitally used to control or assert the established digital ID.
The Individual chooses appropriate Attributes to submit an Identity Claim to the Identity System

The identity system carries out the process of Verification and in some cases, Deduplication to examine the identity claims of the individual.

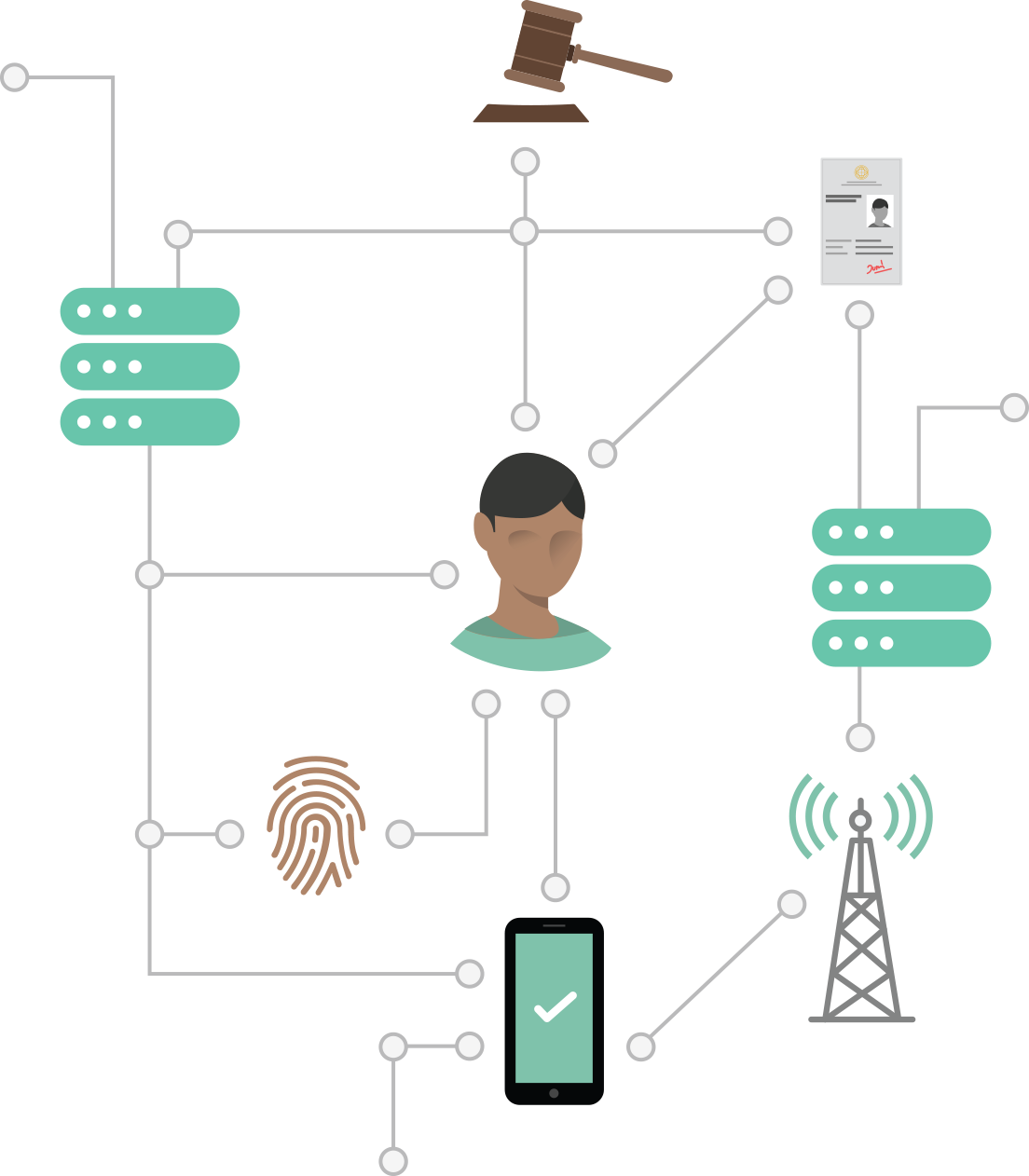
If the processes are successful, then the identity system issues a digital identity to the individual, in the form of an Identity Artifact, and assigns an Identity Credential for future Authentication.
Attribute
An attribute is any property, characteristic, or quality, that is inherent to or ascribed to an Individual, and can be associated with them in a stable or reliable manner.
Name, Age, Sex, Place of Birth, Address, Fingerprints, Signature
Identity Claim
During the process of Identification, Individuals enrolling into the Identity System are often required to produce supporting documents which serve as proofs or identity, address etc. In some cases, Identity Claim may also be made through testimonials or certificates from other entities, or through self-assertion in the form of an affidavit or some other means. Based on the priorities of the Identity System such as fraud reduction, inclusivity etc., the standard for what is an acceptable Identity Claims could vary.
Existing Civil Registration Document, Testimonials, Self-asserted Affidavits
Verification
Verification is the process followed during Identification to check the Identity Claims of an Individual, and ensure that they are the true owner of the claimed Identity and the related evidence/documents. This could include inspecting breeder documents such as a birth certificate to verify the date of birth claimed by the entity, or examining a photo ID card to verify other attributes of appearance, name, sex, etc., by the enrolling agent during the Identification process.
Deduplication
Deduplication is a process undertaken during Identification in some Identity Systems to establish the uniqueness of individuals. It typically involves digitally comparing biographic or biometric data submitted by Individuals against previously enrolled records to determine if there is already a record of the Individual.
Identity Artifact
An identity artifact is a document or object, which can be both physical or digital, that is issued to an Individual at the end of the process of Identification, that facilitates in establishing their Identity. The Identity Artifact will usually involve a registration number assigned to the Individual.
Smart Identity Card, Registration Number, Paper Identity Document
Identity Assurance
Identity assurance is the ability to determine, with some level of certainty or assurance, that a claim to a particular identity made by an Individual can be trusted to actually be the claimant’s true identity. The mapping of this assurance in terms of its overall level, derived from both the quality of the identification process and the strength of the authentication credential used when asserting the identity, is termed its Level of Assurance (LOA).
Seeding
Seeding is the mapping of identity records in an existing database with those in another database, typically through a unique identifier. For instance, in India, Aadhaar numbers of residents are being seeded into the service delivery database of public and private service providers.
Authentication
Authentication is the process of establishing confidence that an Individual is who they claim to be. This involves using an Identity Credential, that was bound to the Identity during the process of Identification (such as fingerprints, a password, a smartcard, etc) to assert that it is within the control of the Individual whose identity is being asserted. This is done through a process established within the Identity System to digitally check the Identity Credential usually against the Identity Artifact.

The Individual uses their Identity Credential to authenticate themselves, often using the digital interface of the Relying Party.

Various relying parties depend on the Identity System to verify the identity of the individual.

If authentication is successful, the relying party permits the individual to carry out the intended activity of transaction using their digital identity.
Identity Credential
An identity credential is any document, object, or data structure, that can digitally affirm the Identity of an Individual through some method of Authentication in an Identity System. There are several kinds of factors that could be used as Identity Credentials.
Smartcards, Biometrics, Passwords, OTPs
Knowledge Factors
In some Identity Systems, the process of authentication is carried by testing for information that the Individual is expected to know. These include Identity Credentials such as passwords and PINs.
Possession Factors
In some Identity Systems, the process of Authentication is carried out through the use of an object that is supposed to be in the possession and control of the Individual. It includes a card, or mobile phone on which they receive an OTP, or a token device on which they receive a code.
Inherence Factors
These factors rely on the use of physical attributes of the Individual that are digitally measurable for Authentication such as fingerprints, iris scans, facial recognition etc.
Behavioral Factors
These factors rely on measurements of behavioral aspects of an individual such as gait, voice patterns for Authentication.
Multi-Factor Authentication
A system workflow that requires more than one factor for the Authentication of the Individual. In Estonia, the use of both the card and PIN is an example of multi-factor authentication.
Relying Party
A relying party is an entity that uses the Authentication mechanism provided by an Identity System to verify the Identity of an Individual, in order to process a transaction or grant access to a system, or information, or a service. Based on the nature and purpose of the Identity System, relying parties can be both government bodies or private actors.
Banks, Telecom Service Providers, Hospitals
Authorisation
Authorisation is the act of the Individual determining what actions may be performed on their behalf, or if their personal data may be accessed, based on the asserted and authenticated Identity. The process of authorisation involves the use of the digital identity to undertake activities and transactions (both financial and otherwise). It is this aspect of digital identity which leads to both its oft-mentioned benefits such as ease of doing business, cost effectiveness and speedy transactions; as well as its prominent risks such as profiling, digital trail connecting disparate activities and discriminatory effects.







